sudo on the client, and have someone create the non-root tunnel on the server. ssh has a "-w" that "Requests tunnel device forwarding with the specified tun(4) devices between the client (local_tun) and the server (remote_tun)." One can create a tun device on Linux that is owned by a non-root user via the iproute2 command. There is an excellent post on this at http://backreference.org/2010/03/26/tuntap-interface-tutorial/ and its owner was a great help to me. I'm connecting a Mac to an Ubuntu machine; the incantations will vary a little if you choose different Unixs. The iproute2 that comes with Ubuntu 12 isn't new enough, so I grabbed a newer one and built it:# does not do the trick, too old.
server$ iproute2-3.7.0$ ip -V
ip utility, iproute2-ss111117
# is new enough
server$ iproute2-3.7.0$ ip/ip -V
ip utility, iproute2-ss121211
One can create an non-root tun via
server$ sudo iproute2-3.7.0/ip/ip tuntap add dev tun9 mode tun user YOU group YOU
One can list all the tun devices via
server$ sudo iproute2-3.7.0/ip/ip tuntap list
server$ sudo iproute2-3.7.0/ip/ip tuntap del dev tun9 mode tun
server$ sudo ifconfig tun9 10.10.10.10 pointopoint 5.6.7.9 up
Make sure the server is routing
server$ cat /proc/sys/net/ipv4/ip_forward
1
server$ sudo arp -sD 5.6.7.9 eth0 pub
On the client, we first connect via ssh
client$ sudo ssh -vvv -w 0:9 YOU@5.6.7.8
client$ sudo ifconfig tun0 5.6.7.9 10.10.10.10 up
client$ sudo route add -net 5.6.7 5.6.7.9
Now things get a little tricky. You want to make the gateway on the server network be the default gateway to complete the VPN. First though, one must tell the client to continue to use its own gateway to get to the server and not use the default
client$ sudo route add -host 1.2.3.1 5.6.7.8
sudo route add default 5.6.7.1
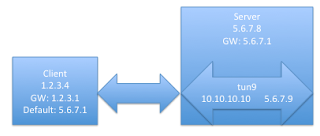
and you're done. Teardown is the opposite, as they say. This is all a little tricky and requires a little routing magic, but it's useful when SSH is all you have.



2 comments:
Nice, but, if I can't access the server as root, very likely I cannot access it via sudo either.
That is true -- I assume a friendly sysadmin to set it up initially.
Post a Comment